The US is warning about “pro-Russian hacktivists” breaking into IT systems at critical infrastructure providers, such as water systems, to potentially cause havoc.
On Wednesday, several US agencies—including the FBI, NSA, and Cybersecurity and Infrastructure Security Agency (CISA)—published an alert about the hacktivists groups targeting sectors including wastewater treatment, dams, energy, and agriculture.
So far, the hacking efforts have been “mostly limited to unsophisticated techniques” to manipulate small-scale IT systems, the agencies said, resulting in attacks that were more of a nuisance than an actual disruption—like “causing water pumps and blower equipment to exceed their normal operating parameters.” Nevertheless, the agencies are concerned the hacking activities could lead to more “physical threats.”
“In each case, the hacktivists maxed out set points, altered other settings, turned off alarm mechanisms, and changed administrative passwords to lock out the WWS (Water and Wastewater Systems) operators,” the alert says. “Some victims experienced minor tank overflow events; however, most victims reverted to manual controls in the immediate aftermath and quickly restored operations.”

(Credit: CyberArmyofRussia_Reborn)
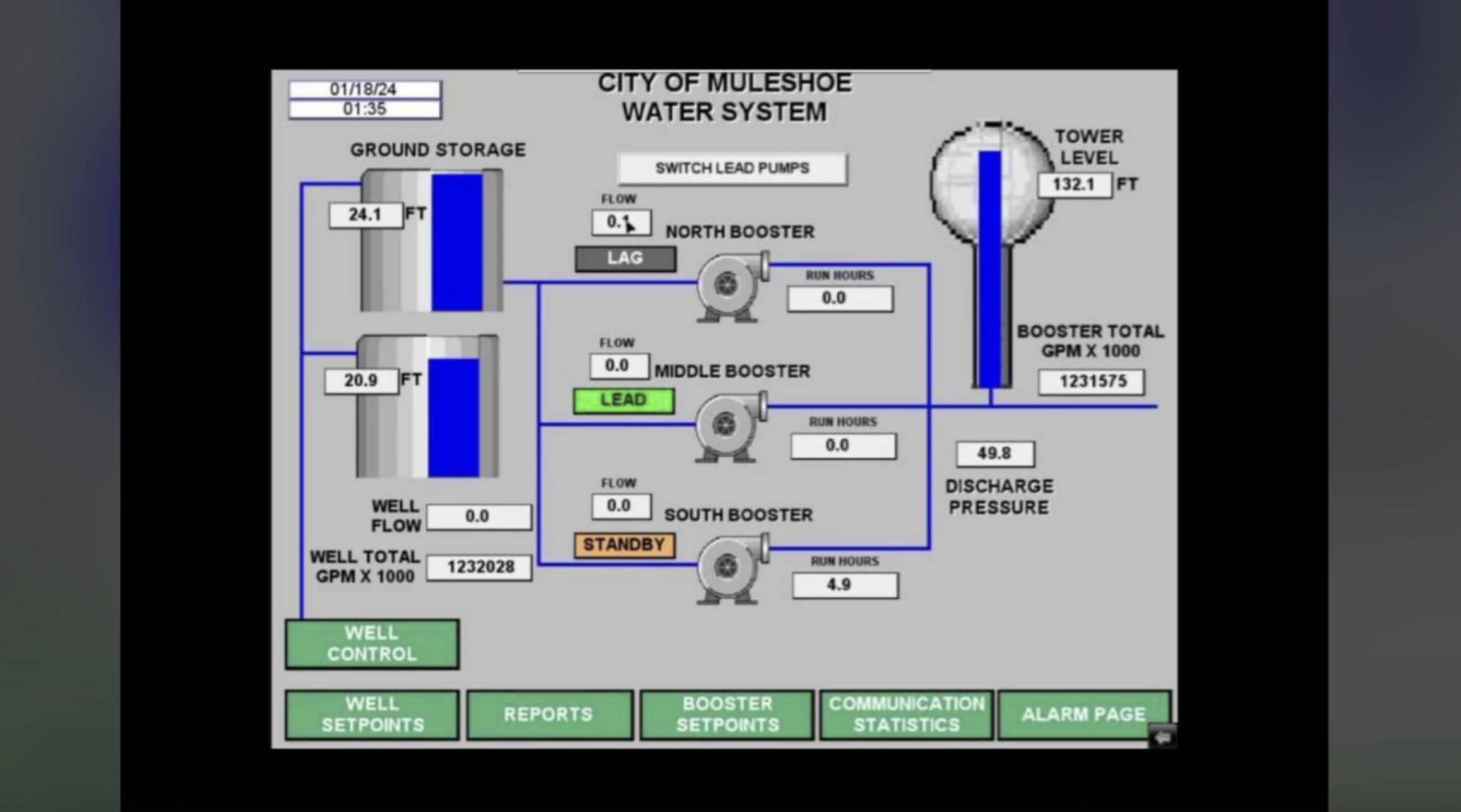
The US published the warning two weeks after Google’s Mandiant cybersecurity arm uncovered evidence that a pro-Russian hacktivist group called the “CyberArmyofRussia_Reborn” is tied to a notorious Kremlin-backed hacking group called Sandworm. The same group reportedly took over the water systems in Muleshoe, Texas, in January and caused a water tank overflow.
Recommended by Our Editors
In a press briefing on Wednesday, CISA declined to identify the pro-Russian hacktivist groups or say if they’re linked to Sandworm. However, the agency indicates the threat should be relatively easy to stop. That’s because the hacktivists are infiltrating the IT systems by exploiting default passwords and weak login credentials.
In response, the federal agencies are urging critical infrastructure providers to remove default logins in favor of strong, unique passwords and implement multi-factor authentication. The alert also advises infrastructure providers to disconnect their operational systems from the public-facing internet or implement a firewall with multi-factor authentication in place.
Like What You’re Reading?
Sign up for SecurityWatch newsletter for our top privacy and security stories delivered right to your inbox.
This newsletter may contain advertising, deals, or affiliate links. Subscribing to a newsletter indicates your consent to our Terms of Use and Privacy Policy. You may unsubscribe from the newsletters at any time.






