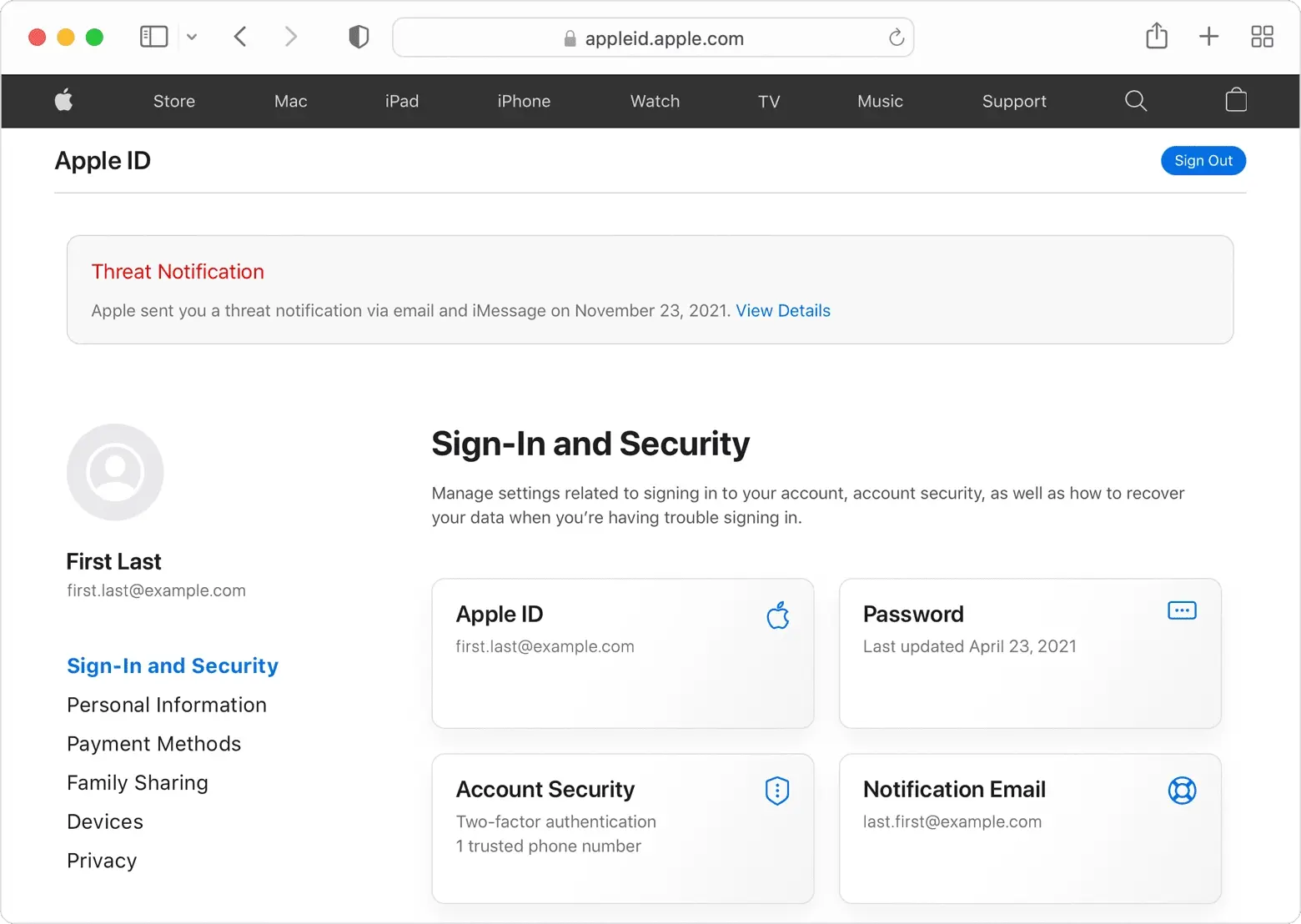
Apple recently sent out threat notifications to iPhone users in 92 countries and regions. The notice warns users of potential spyware attacks targeting their devices. The company detected a sophisticated spyware attack aimed at compromising iPhones associated with users’ Apple IDs. Apple did not disclose the identity of the attacker or the country or region where users were notified. However, in the warning to select users, the company wrote
“Apple has detected that you are being targeted by a spyware attack that attempts to compromise the iPhone associated with your Apple ID remotely. This attack is likely to be specifically targeting you, no matter who you are or what you do. While this type of attack can never be accurately detected, Apple is confident in this warning – please take it seriously.”
Spyware Threat Notification by Apple
Apple issued a threat notification to iPhone users, alerting them to a spyware attack that aims to remotely compromise their devices. The warning emphasized the targeted nature of the attack, indicating that it is likely directed at specific individuals. Despite the challenge of accurately detecting such attacks, Apple urged users to take the warning seriously, emphasizing the gravity of the situation.
To avoid getting targeted, users should practice good cyber hygiene, including updating devices and apps, using strong passwords, and enabling multi-factor authentication. Apple introduced Lockdown Mode in September 2022 with iOS 16, iPadOS 16, MacOS Ventura, and watchOS 10 to reduce the attack surface that can be exploited by highly targeted mercenary spyware. This mode blocks most message attachment types, certain web technologies, and FaceTime calls from new devices. It will be good for users to ensure that this mode is active. It will help to prevent the possibility of a spyware attack.

Frequency and Scope of Threat Notifications
Since 2021, Apple has been sending out threat notifications to users multiple times each year. This system covers more than 150 countries and regions. Spyware attacks differ from regular cybercriminal activities and consumer malware due to their specialized and targeted nature. These attacks are highly sophisticated, costly, and transient, posing challenges in detection and prevention. The majority of users are unlikely to be targeted by such attacks. Spyware attacks cost millions of dollars and are often short-lived. This makes them harder to detect and prevent. However, vast majority of users will never be targeted by such attacks.
These notifications are part of Apple’s efforts to alert and help users whom state-sponsored attackers may have targeted. The notification system informs and assist users who may be individual target due to “who they are or what they do”. However, the system is not foolproof, and some notifications might be false positives. Also, some attacks may not be detected at all due to the sophistication of state-sponsored attackers.
Gizchina News of the week
Apple’s threat notifications never have any links to click,. Users should never install any apps or profiles. They should not also provide Apple ID passwords or verification codes via email or over the phone.
Recommendations for Protection
To safeguard against general cybercriminals and consumer malware, Apple provides several key suggestions for users:
- Update Device Software: Ensure your device is running the latest software version to benefit from the most recent security patches and fixes.
- Password Protection: Secure your device with a strong password to prevent unauthorized access.
- Two-Factor Authentication: Enable two-factor authentication and use robust passwords for your Apple ID to enhance security.
- App Installation: Only download and install apps from the official App Store to minimize the risk of malware.
- Strong Online Passwords: Use unique and strong passwords for online accounts to prevent unauthorized access.
- Avoid Clicking Unknown Links: Refrain from clicking on links or attachments from unfamiliar senders to mitigate the risk of phishing attacks.

Apple’s proactive approach in notifying users about potential spyware attacks is quite good. By following the recommended security measures and staying vigilant against cyber threats, iPhone users can enhance their device’s security posture.
Conclusion
Apple’s threat notifications, which have been sent to iPhone users in numerous countries, serve as a warning about potential state-sponsored attacks targeting specific individuals. These alerts are designed to inform and assist users who may have been targeted by these sophisticated and well-funded attackers. The attacks are challenging to detect and prevent due to their targeted nature and the significant resources invested in them.
Apple’s threat notifications are typically sent to individuals who are more likely to be targeted, such as political leaders, journalists, and activists. The company relies on imperfect and incomplete threat intelligence signals to detect these attacks, acknowledging the possibility of false alarms or undetected attacks.
To verify the authenticity of an Apple threat notification, users can sign in to appleid.apple.com. If a legitimate threat notification goes out, it will clearly display at the top of the page after signing in. Apple advises users to follow best practices for security, such as updating devices to the latest software, protecting devices with a passcode, using two-factor authentication and strong passwords for Apple ID, installing apps from the App Store, using strong and unique passwords online, and avoiding clicking on links or attachments from unknown senders.
While the controversy surrounding these threat alerts has stirred up a political storm in some countries, Apple has maintained a guarded response, refusing to provide specific details on how it flags recipients or attributing the threat notifications to any specific state-sponsored attacker. The company emphasizes that detecting such attacks is an ongoing challenge due to the evolving nature of these sophisticated threats.