An updated version of the XLoader malware for Android devices doesn’t require any user interaction to launch once installed, according to researchers at McAfee (via BleepingComputer). Of course, you still need to click the malicious link in an SMS message to download and install the malware, but this XLoader variant doesn’t require users to manually launch the malware anymore.
Right now, the malware is being distributed through SMS texts on Android devices. If you’re targeted, the SMS text will include a shortened URL that, if clicked on, will direct you to a website to download an Android APK installation file for a mobile app. McAfee says that, “While the app is installed, their malicious activity starts automatically.”
The malware will run silently in the background, gaining access to all kinds of personal, private data on your Android device, including photos, messages, contacts, and potentially banking information. Luckily, the malware is pretty easy to spot and you might already be protected if Google’s Play Protect service is enabled on your Android device. Here’s what to look for, and how to see if Play Protect is active.
How to spot the new XLoader malware
XLoader—also known as MoqHao malware—is likely created by ‘Roaming Mantis,’ a financially-motivated threat actor, and McAfee identified some malicious pop-up messages in the malware’s code in English, Korean, French, Japanese, German, and Hindi, which indicates the malware’s current targets.
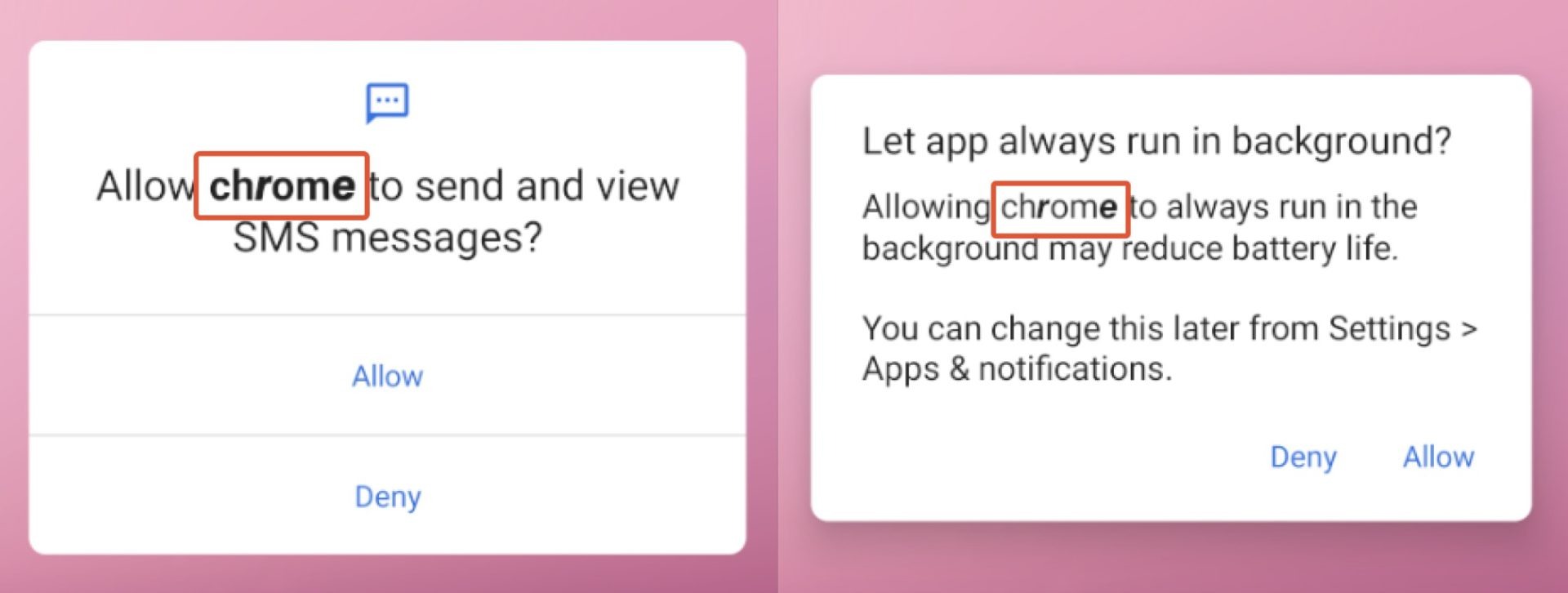
If you’re in an area that primarily speaks one of those languages, you might be at risk, but the warning signs that something’s off are pretty clear. In permission requests during the malicious app’s first launch, it’ll masquerade as Google Chrome, but you’ll notice some letters are bolded while others aren’t.
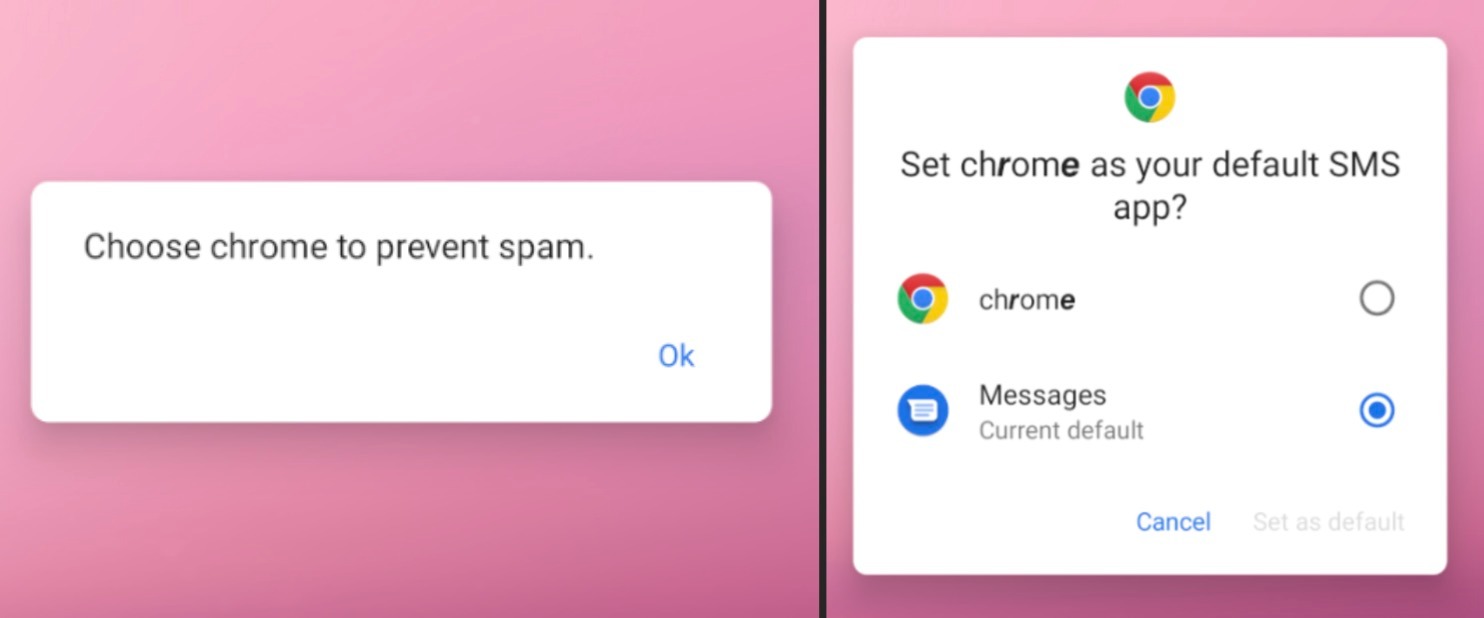
After those initial requests, the malicious app will ask you to set “chrome” as your default SMS app, citing the reason “to prevent spam” to convince you it’s the right decision. Again, you’ll spot randomly bolded letters here as a warning sign that something’s off.
You should be on the lookout for suspicious-looking phishing URLs from Pinterest profiles, as this is a primary way the XLoader malware is targeting victims and evading detection right now. There are about 20 commands outlined by McAfee that the malware can execute right now. These 5 pose the biggest threat to your personal data:
- get_photo: Sends all photos on your device to the hacker’s command and control (C2) server
- getSmsKW: Sends all SMS messages on your device to the C2 server, which could possibly contain sensitive information sent to family and friends
- sendSms: Lets the XLoader malware send SMS messages from your device, potentially spreading phishing links to your friends and family
- gcont: Exports your contacts list to the C2 server, giving the hackers direct contact info for targeted phishing attacks
- getPhoneState: Grabs your device’s identifying information, like its IMEI, SIM number, Android ID, and serial number
In its recent report, McAfee explains that it has told Google about the XLoader malware’s technique of bypassing manual user launch to start running the app, and that Google is “already working on the implementation of mitigations to prevent this type of auto-execution in a future Android version.”
McAfee then goes on to explain that “Android users are currently protected by Google Play Protect, which is on by default on Android devices with Google Play Services.”
To see if Play Protect is active, open the Google Play app, tap on your profile icon in the top right corner, select Settings, and tap About to open the dropdown menu. At the very bottom, under Play Protect Certification, there should be a short message that reads Device is certified.